The Relevance of Cyber Safety in Protecting Your Digital Assets
In today's electronic period, the significance of cyber protection in securing your digital assets can not be overstated. As technology breakthroughs, so do the strategies of cybercriminals, making robust cyber defenses vital for individuals and services alike. Carrying out efficient cyber protection techniques is not just a referral however a requirement to minimize risks and make sure connection.
Recognizing Cyber Dangers
In the rapidly developing landscape of digital technology, recognizing cyber threats is extremely important for securing electronic possessions. The term "cyber hazards" includes a large selection of destructive tasks aimed at endangering the honesty, discretion, and schedule of info systems.

Comprehending the inspirations behind these risks-- be it financial gain, reconnaissance, or hacktivism-- is important for establishing efficient countermeasures. This understanding empowers companies to expect prospective risks, tailor their defenses, and eventually protect their useful digital possessions from cyber enemies.
Secret Cyber Safety Practices
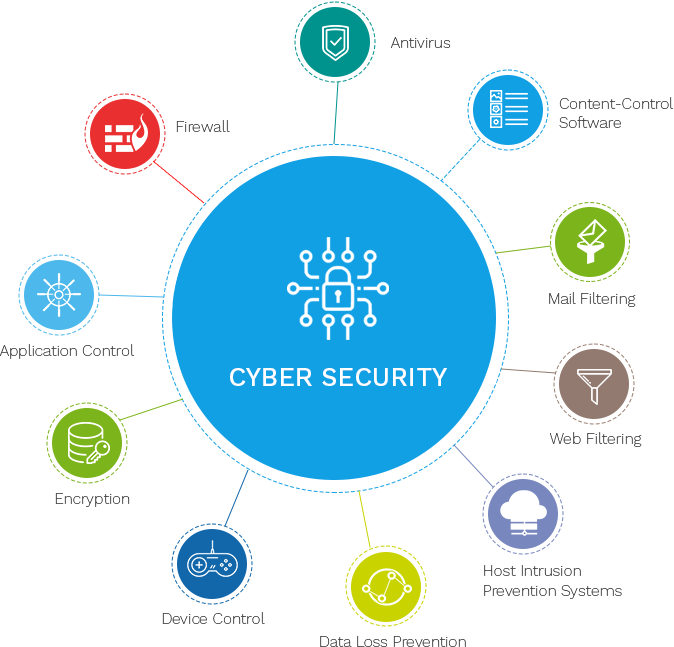
Network safety is one more essential aspect - Best Cyber Security Services in Dubai. This entails making use of firewalls and invasion discovery systems to monitor and regulate outward bound and incoming network traffic, efficiently obstructing dubious tasks. Regularly upgrading software and systems is similarly crucial, as it patches recognized susceptabilities that cybercriminals can make use of
Data file encryption is a vital technique that ensures delicate info is just easily accessible to accredited customers. By transforming data right into a code, it ends up being unreadable without the decryption trick, hence protecting it from unauthorized accessibility during transmission or storage space.
Informing employees and individuals about cyber protection ideal practices is likewise vital - Best Cyber Security Services in Dubai. Regular training sessions can elevate understanding about typical risks like phishing and social engineering, encouraging people to recognize and stay clear of prospective threats. By incorporating these key techniques, companies can build a resistant defense against the ever-changing landscape of cyber hazards
Protecting Personal Information
Safeguarding personal data has become a necessary in today's digital age, where the quantity of information traded online is staggering. This information encompasses every little thing from social safety numbers to personal health and wellness records, and its defense is vital for preserving personal privacy and protection. Individuals must be cautious in ensuring that their personal info is not endangered, as breaches can cause identity burglary, financial loss, and reputational damage.

Recognition of phishing attempts is critical, as cybercriminals often make use of deceitful emails and websites to steal personal information. Individuals need to confirm the resource of unrequested communications and prevent clicking on dubious web links. Finally, protecting individual devices with antivirus software application and firewall programs can better strengthen defenses versus unauthorized accessibility and possible dangers.
Shielding Organization Information
While safeguarding personal information stays a top priority for people, businesses encounter the broader difficulty of safeguarding vast quantities of delicate details that drive their operations. Applying robust cyber safety and security actions is not just an option yet an essential need for services of all sizes.
To successfully safeguard organization info, a multi-layered security strategy is essential. This should include firewall programs, security, breach detection systems, and routine security audits.
Moreover, companies ought to establish and consistently upgrade occurrence response strategies. Being gotten ready for possible breaches makes certain quick action to minimize damage. By purchasing comprehensive cyber security techniques, businesses not only shield their assets but also strengthen depend on with their clients and companions, inevitably securing their market placement and future growth.
Future Trends in Cyber Security
As the digital landscape quickly advances, future patterns in cyber safety and security are poised to redefine just how companies safeguard their electronic assets. One prominent fad is the rise of expert system (AI) and artificial intelligence (ML) in danger discovery and reaction. These modern technologies enable much faster recognition of anomalies and possible hazards, allowing for more effective and automatic feedbacks to cyber cases. Organizations are increasingly embracing AI-driven tools to improve their cyber protection capacities.
As remote work becomes extra Click This Link prevalent, standard perimeter-based safety and security versions are showing insufficient. The zero-trust method calls for constant verification of gadgets and customers, also within the network, thereby decreasing possible assault vectors.
Furthermore, quantum computing is arising as both a threat and a possibility. While it assures exceptional processing power, it positions dangers to current security approaches. Organizations should prepare for post-quantum cryptography to safeguard their information.
Lastly, privacy-enhancing modern technologies are Read More Here gaining momentum. With enhancing governing focus on information protection, services are purchasing devices that guarantee compliance while maintaining functional performance. These future patterns highlight the ever-evolving and vibrant nature of cyber protection.
Verdict
In a progressively interconnected digital landscape, the application of durable cyber safety and security procedures is vital to secure digital properties from evolving hazards such as ransomware, phishing, and malware. Employing techniques like strong passwords, multi-factor verification, and normal software updates boosts the defense of delicate info, mitigating dangers of identity burglary and economic loss. Structure awareness and taking on innovative security methods foster strength and trust fund, making sure the integrity and connection of both individual and company electronic procedures despite future cyber difficulties.
In today's electronic period, the value of cyber safety in protecting your digital possessions can not be overstated.Applying effective cyber safety and security practices is critical in securing electronic possessions versus developing hazards.As the digital landscape quickly progresses, future patterns in cyber safety and security are positioned to redefine exactly how services shield their digital properties.In an increasingly interconnected digital landscape, the implementation of durable cyber safety actions is essential to secure digital possessions from developing threats such as malware, ransomware, and phishing. Building awareness and adopting sophisticated protection strategies foster strength and depend on, guaranteeing the integrity and connection of both individual and service electronic procedures in the face of future cyber challenges.